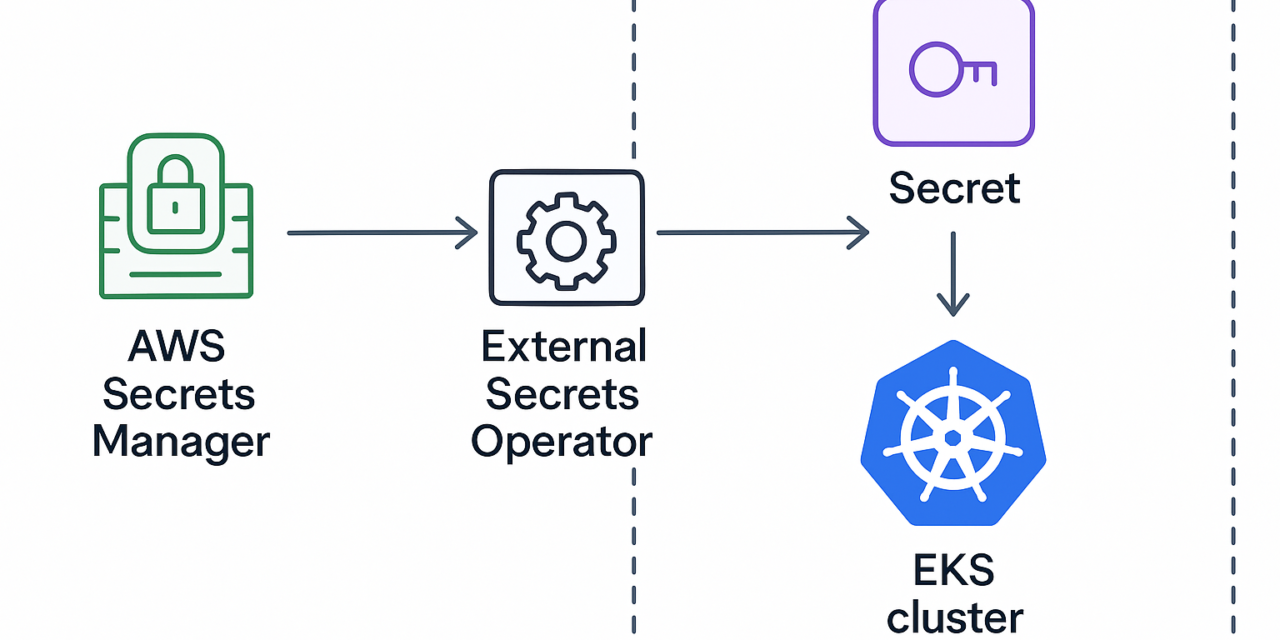
Managing secrets securely in Kubernetes can be challenging, especially when integrating with cloud-native services like AWS Secrets Manager. In this article, I’ll walk you through how to sync secrets from AWS Secrets Manager into Kubernetes secrets on Amazon EKS using the External Secrets Operator (ESO).
Why Use External Secrets Operator?
ESO is an open-source Kubernetes operator that allows you to sync secrets from external providers (like AWS Secrets Manager) into Kubernetes secrets.
Benefits:
- Automatic syncing and rotation of secrets.
- Declarative configuration via Kubernetes manifests.
- Secure integration using IAM Roles for Service Accounts (IRSA).
Step-by-Step Setup on Amazon EKS
Install External Secrets Operator
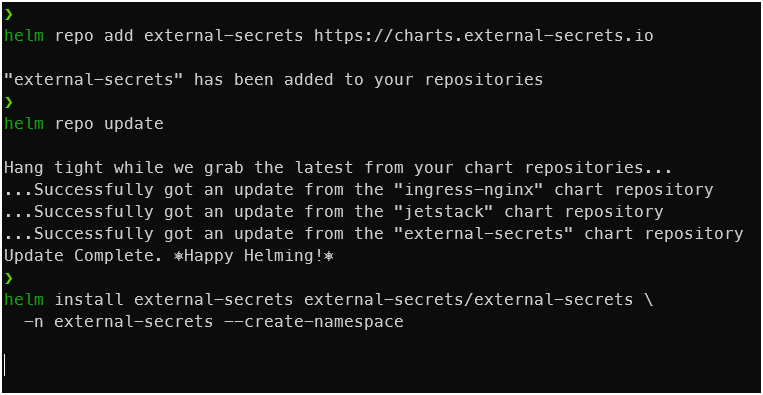
helm repo add external-secrets https://charts.external-secrets.io helm repo update helm install external-secrets external-secrets/external-secrets \ --namespace external-secrets --create-namespace
Enable IAM OIDC Provider for Your EKS Cluster
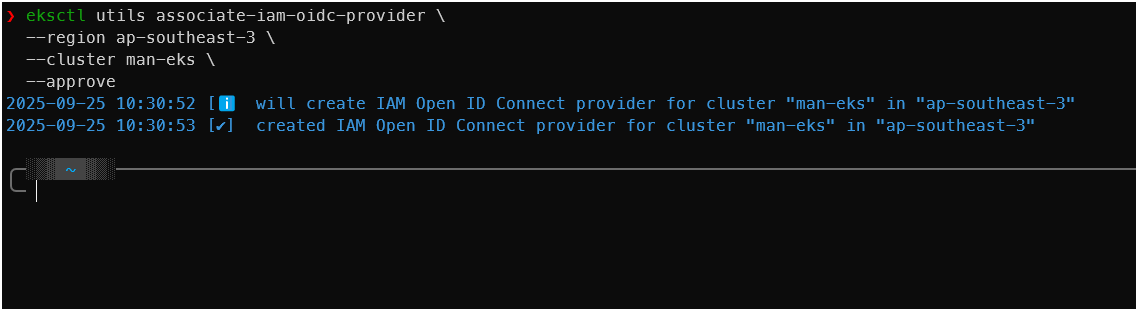
eksctl utils associate-iam-oidc-provider \ --region ap-southeast-3 \ --cluster man-eks \ --approve
Create IAM Policy for Secrets Access
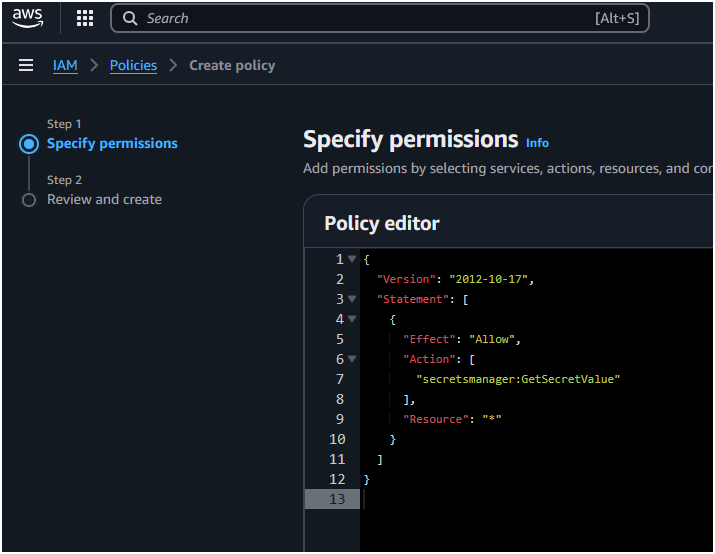
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["secretsmanager:GetSecretValue"],
"Resource": "*"
}
]
}
Create IAM Role and Service Account (IRSA)
eksctl create iamserviceaccount \ --name external-secrets-sa \ --namespace external-secrets \ --cluster man-eks \ --region ap-southeast-3 \ --attach-policy-arn arn:aws:iam::<your-account-id>:policy/eks-secrets-manager\ --approve
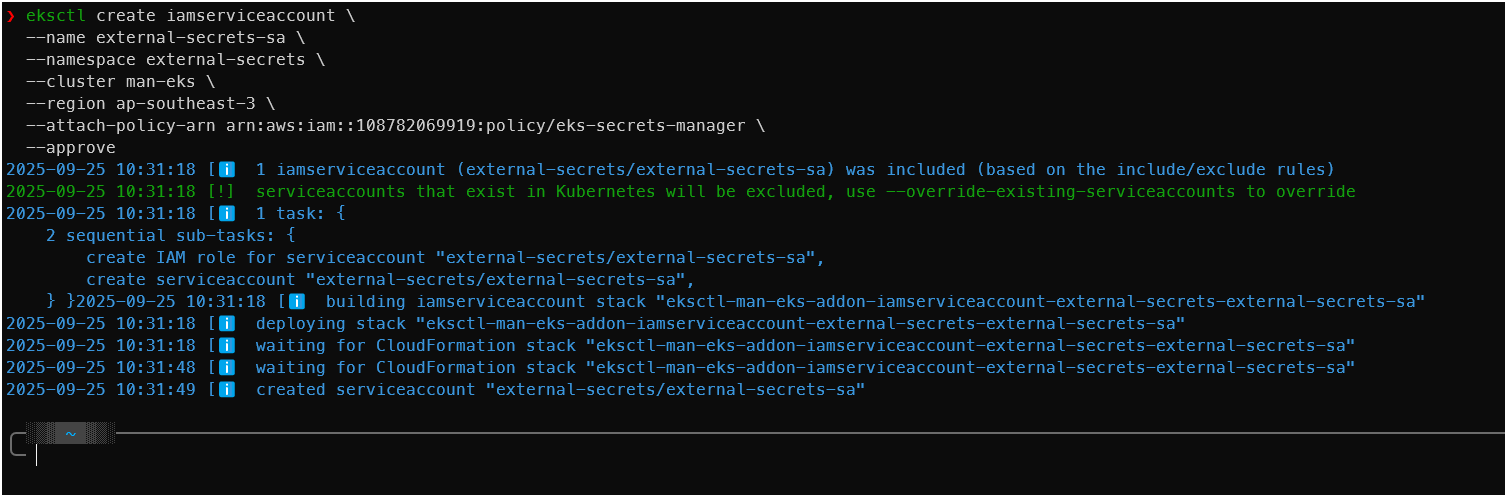
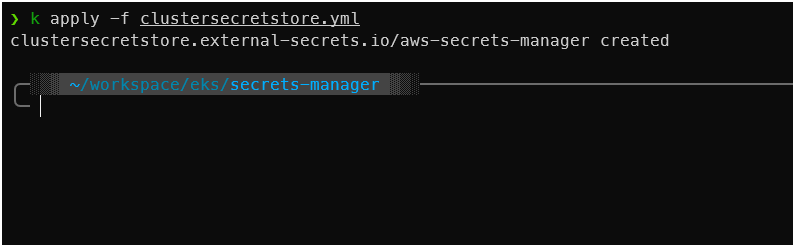
Create ClusterSecretStore
apiVersion: external-secrets.io/v1beta1
kind: ClusterSecretStore
metadata:
name: aws-secrets-manager
spec:
provider:
aws:
service: SecretsManager
region: ap-southeast-3
auth:
jwt:
serviceAccountRef:
name: external-secrets-sa
namespace: external-secrets
apply it
kubectl apply -f clustersecretstore.yml
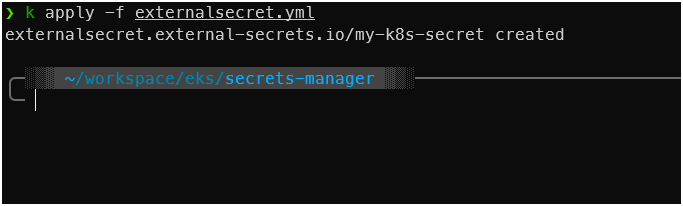
Sync the secrets
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: my-k8s-secret
namespace: default
spec:
secretStoreRef:
name: aws-secrets-manager
kind: ClusterSecretStore
target:
name: my-k8s-secret
creationPolicy: Owner
dataFrom:
- extract:
key: my-aws-secret-name
apply it
kubectl apply -f externalsecret.yml
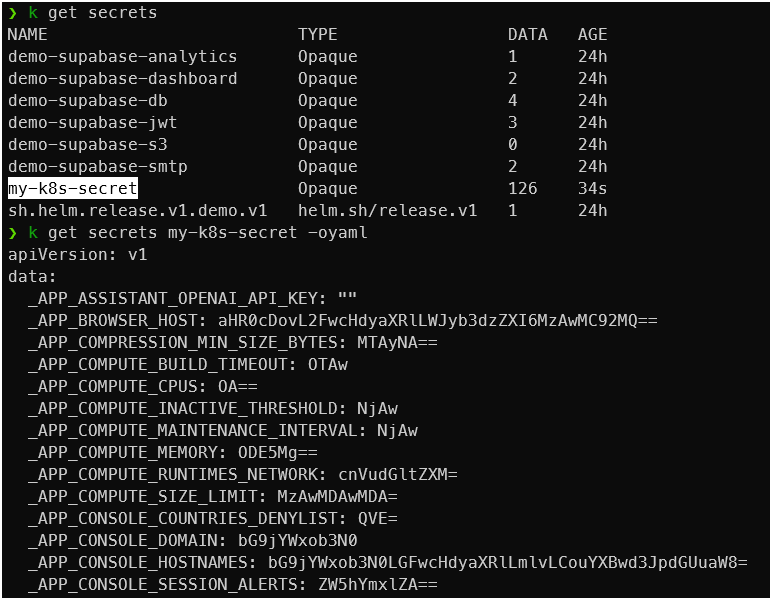
ESO will automatically create a Kubernetes secret named my-k8s-secret in the default namespace, containing all key-value pairs from your AWS Secrets Manager secret. Using ESO with IRSA is a secure and scalable way to manage secrets in EKS. It simplifies secret rotation and reduces manual overhead, making your Kubernetes workloads more secure and cloud-native.
Kube secrets:
AWS secrets manager:
Thank you