HashiCorp Vault is a security management platform used to manage access to sensitive data, such as encryption keys, authentication tokens and passwords. Vault helps ensure that sensitive data is stored securely, by granting access only to those with appropriate access rights.
Here we will try to use vault to be used to store dotenv files of an application or service. The prerequisite is that you have vault installed (in client too, ex: vm server / laptop, we will use vault cli) and root account
Create ACL policy
First, we should to create ACL policy that will be consume by user using root token.
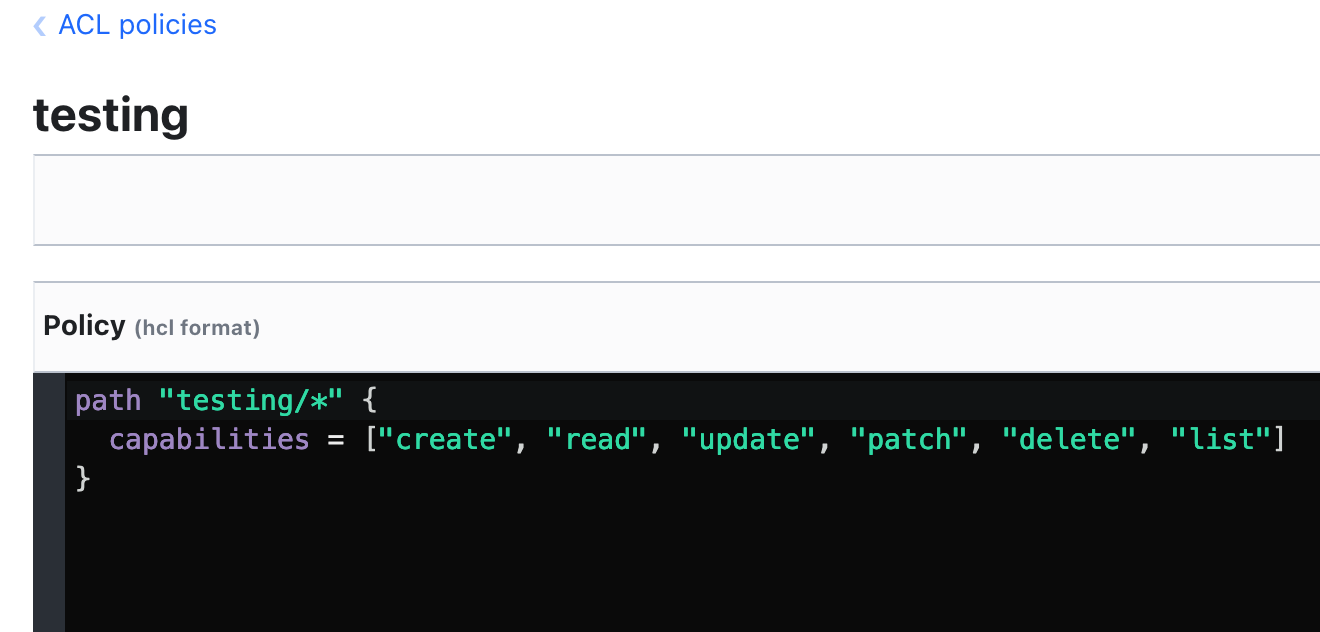
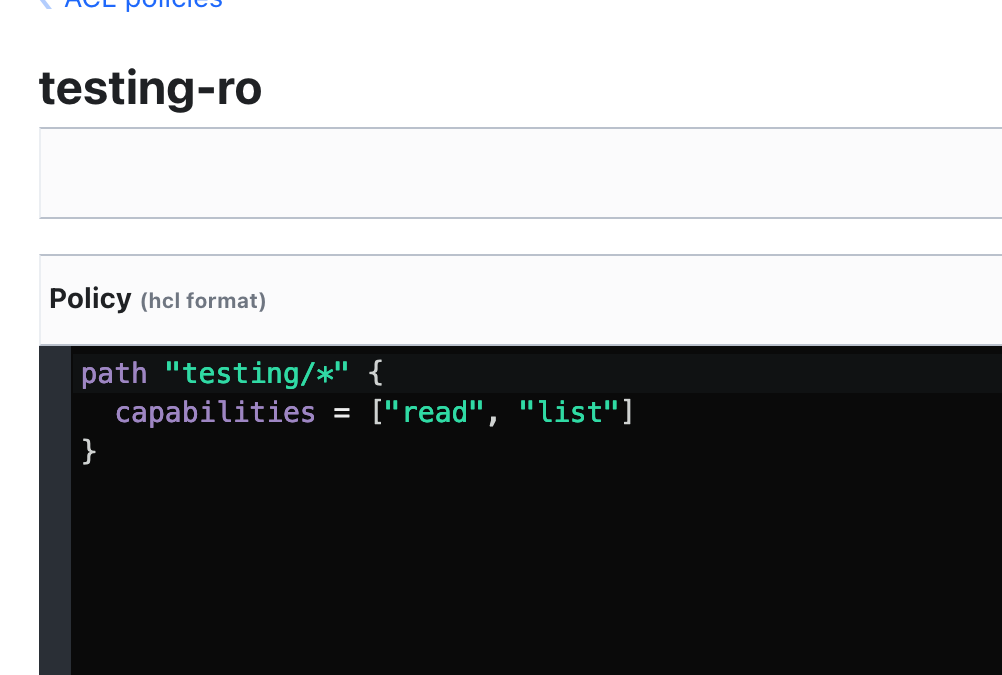
In this example, later we will create an key value secrets in testing/… then we need to define path in the ACL policy. Create account with read-only policy too for apps / services.
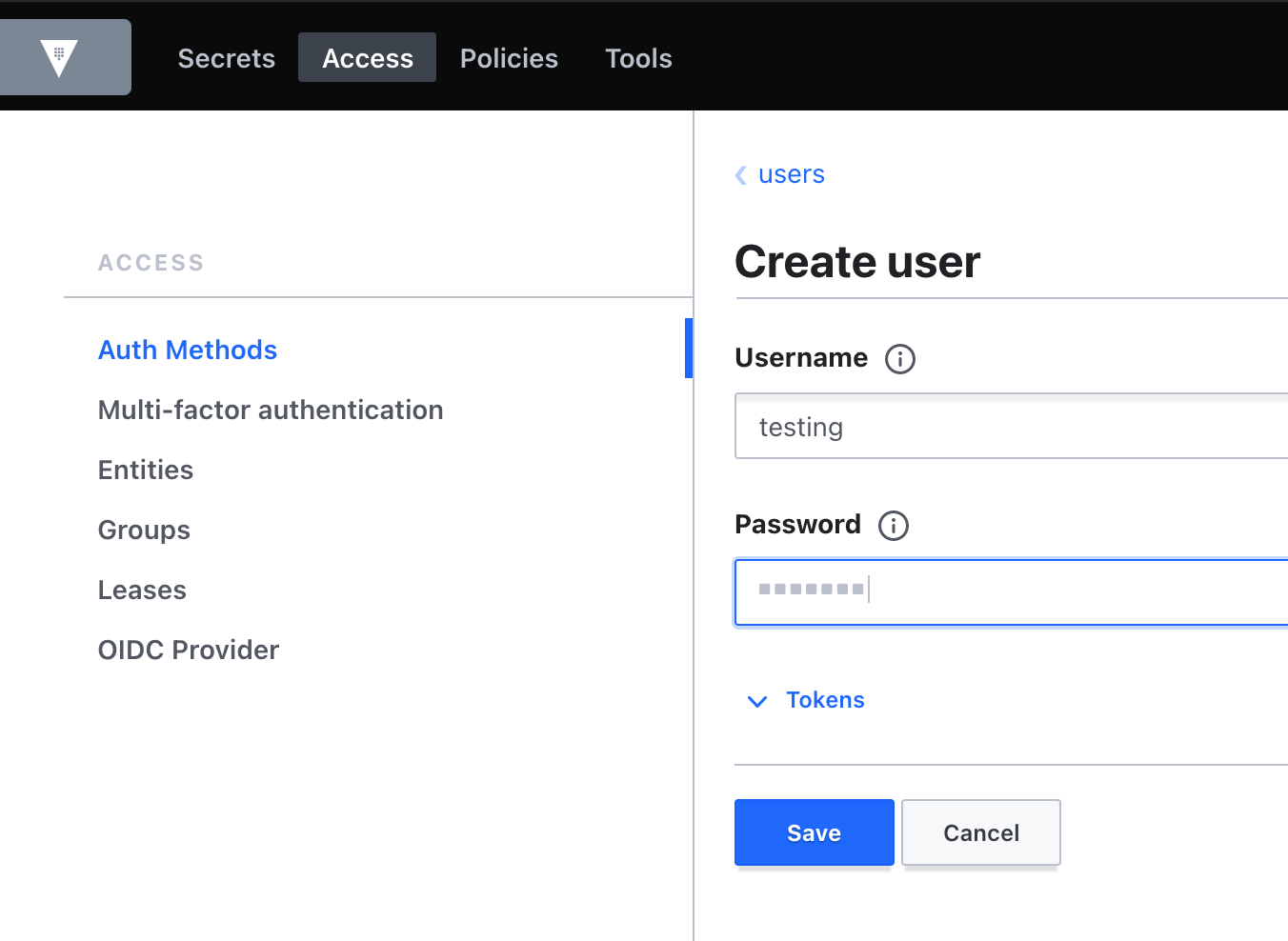
Create user
Second, create user testing for admin and testing-ro for apps / services. We using “user password” method.
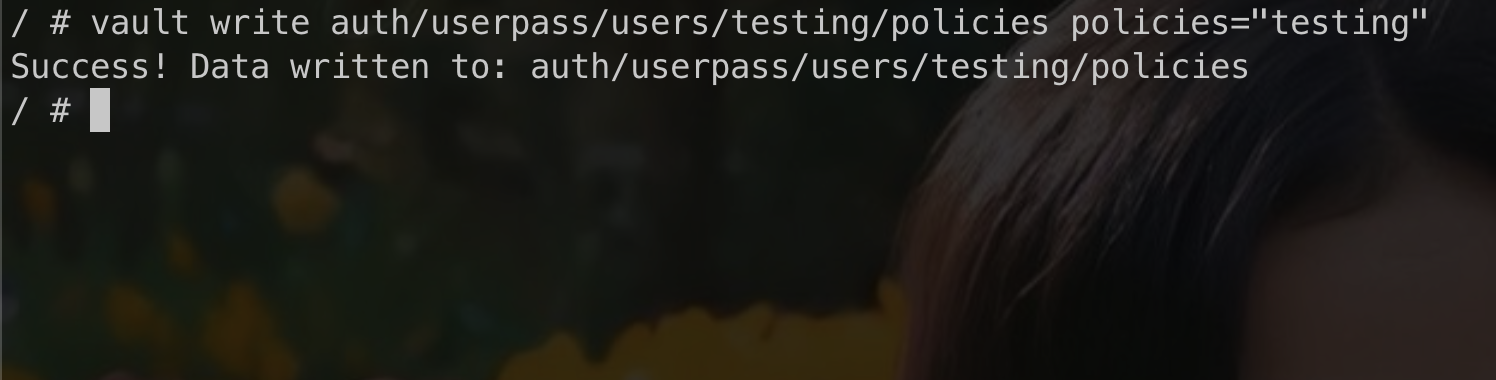
Attach user to policy that we have created earlier. In this section, we have to use vault cli because i doesn’t see attach policy configuration in web ui. don’t forget to use root token.
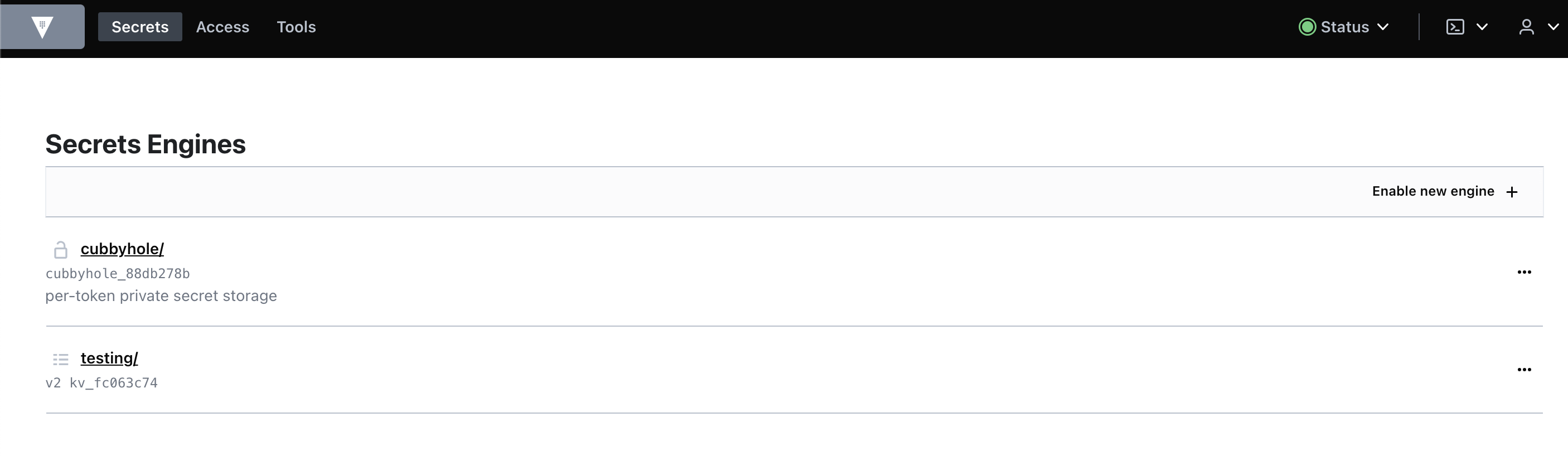
Enable secrets engine ‘testing’ useing root token
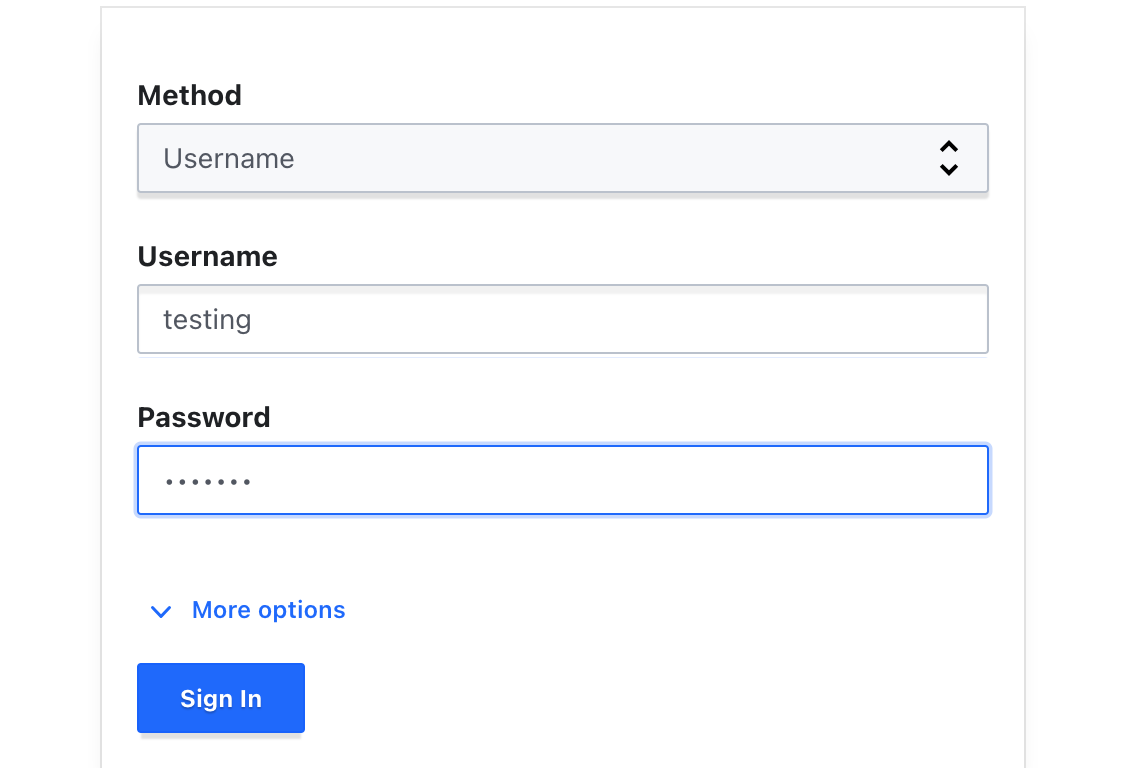
Now, we can use ‘testing’ user for create, read, update, and delete the secrets. login using ‘testing’ user.
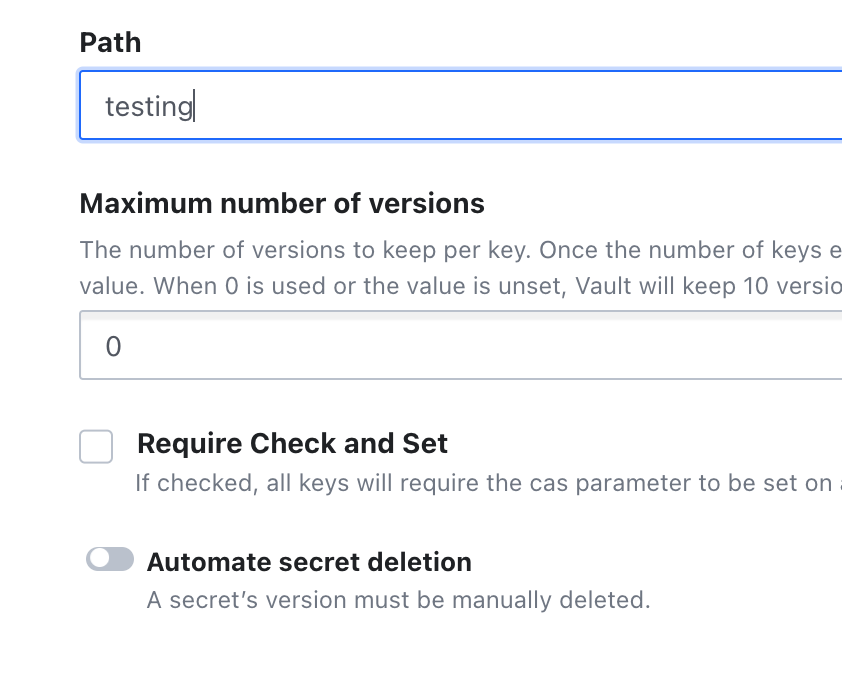
Create an key value secret
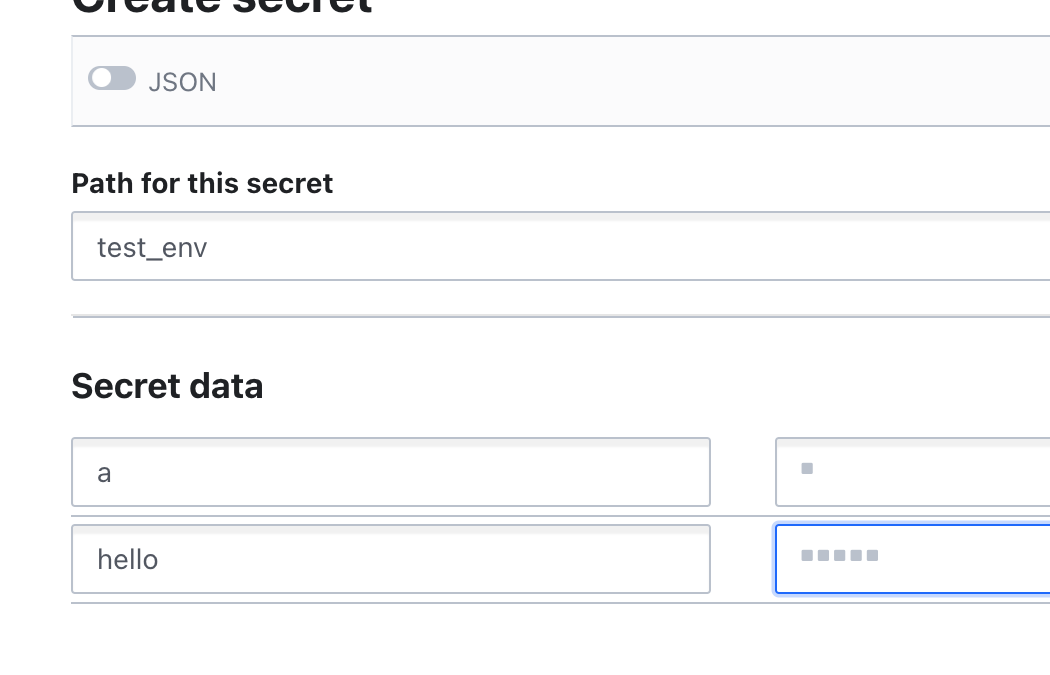
Access using vault cli
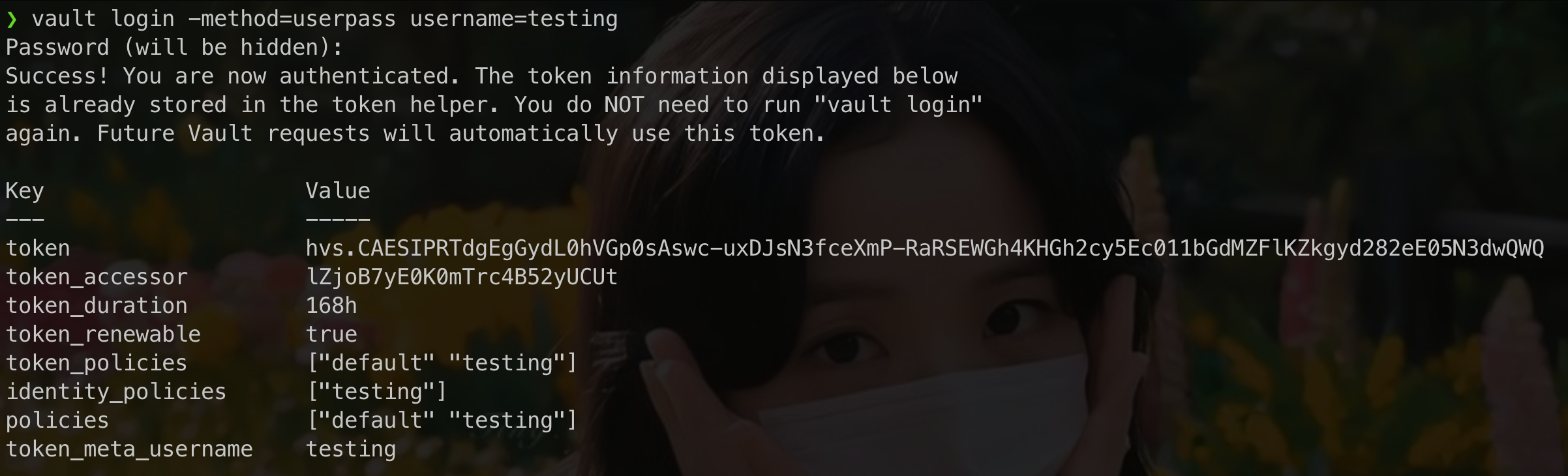
we need login first, login with username that we create in earlier
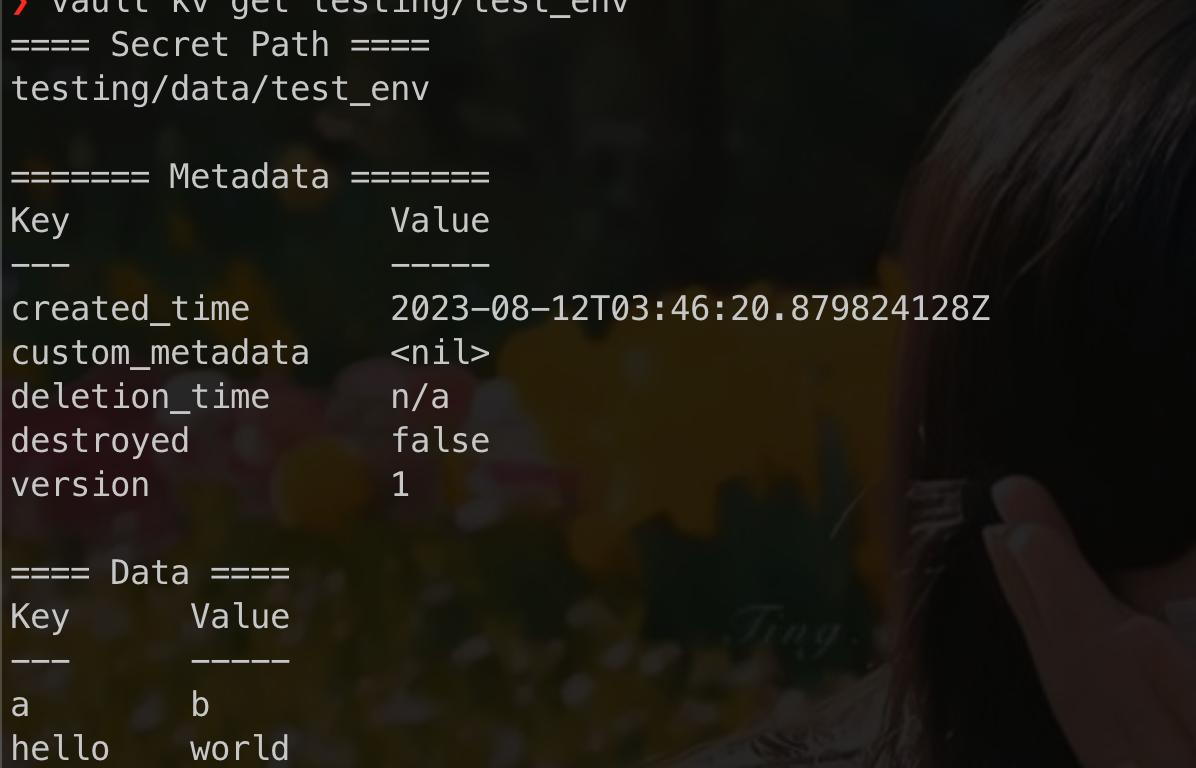
access key value that we create
Save output to .env file
we can get output format to json and process with jq to get key=value output.
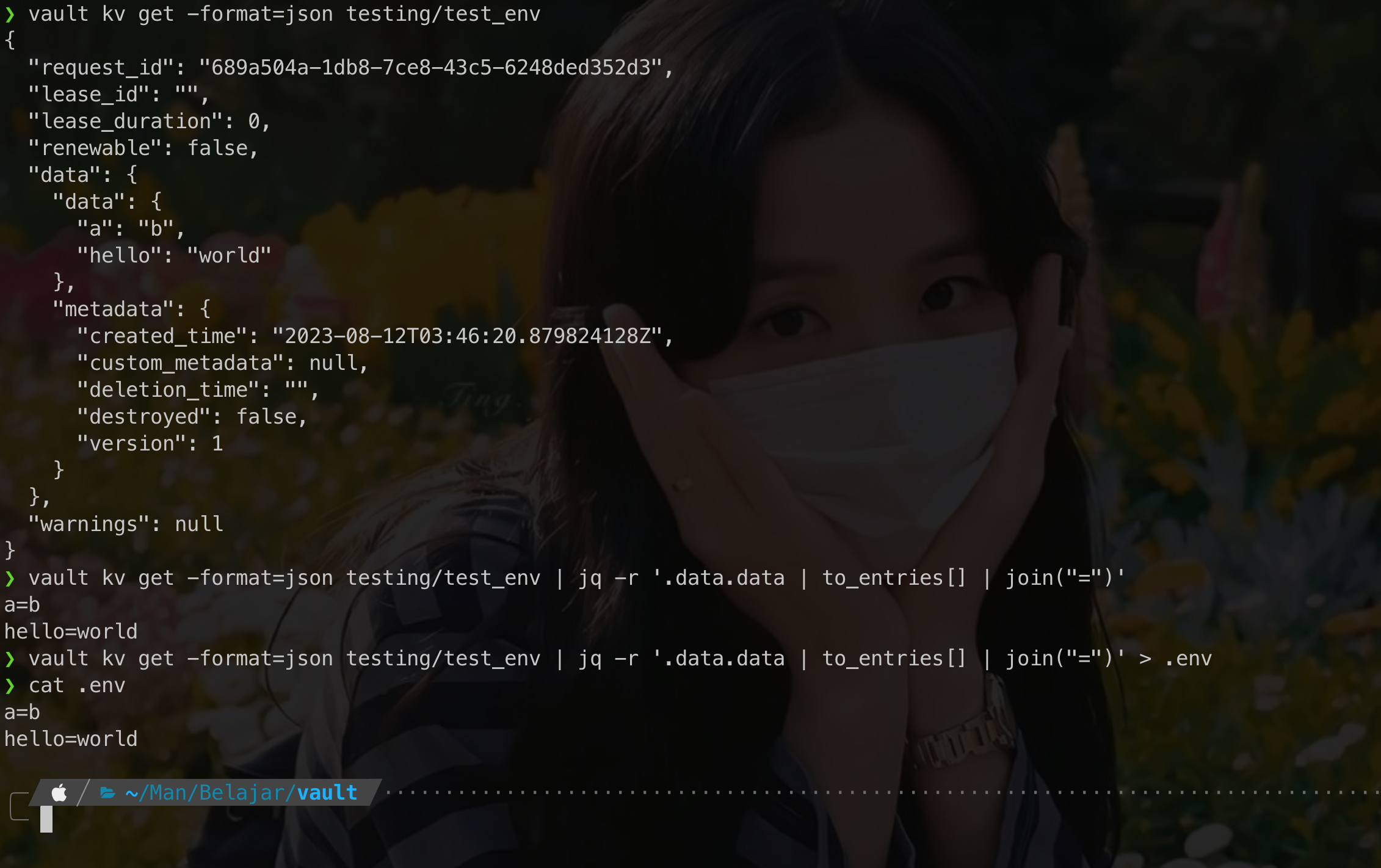
Great! now we can update .env through CI/CD pipeline using vault as secrets management